As threat landscapes intensify and compliance requirements grow more rigorous, simply “shifting security left” no longer guarantees robust supply chain protection. Most organizations leveraging open source experience a continuous rise in sophisticated threats, with malicious packages accelerating year over year. Leaders in security and development are now adopting advanced, holistic strategies to safeguard their software assets and delivery pipelines.
Responding to Emerging Threats and Compliance Pressures
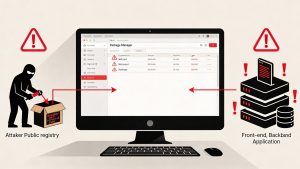
Cyber criminals increasingly bypass legacy defenses by targeting developers directly, leading to notable jumps in reported attacks and supply chain breaches. Industry surveys show nearly one-third of recent exploits stem from software vulnerabilities, closely followed by supply chain incidents. These conditions drive regulated industries to invest in security patterns that address the entire software lifecycle—from upstream components to runtime operations.
Advancing Beyond Hardened Container Images
While many vendors claim to deliver hardened container images with minimal vulnerabilities, enduring security goes further—requiring active removal of extraneous packages and dependencies. Analogous to establishing defensible space during wildfire mitigation, removing nonessential software parts makes containers less susceptible to compromise. Each eliminated package reduces the potential for bugs or exploits, enhancing overall system resilience.
Distroless Containers for Maximum Protection
Distroless containers advance security by stripping away all but the essentials needed for application execution. By eliminating shells, package managers, and standard filesystem tools, these images reduce attack vectors and shrink image size. Such containers are perfect for mature organizations using air-gapped networks, zero-trust architectures, or environments with strict access controls. Though less convenient for debugging, modern tools continually improve usability for distroless deployments.
Strategic Catalog Coverage to Maintain Compliance
Building a comprehensive, secure catalog of approved images and components is crucial. Developers who step outside this “walled garden” introduce compliance and risk gaps. Effective supply chain strategies feature catalogs broad enough to support key projects, allowing platform users to remain compliant while mitigating untracked exposures.
Optimizing Images for Accreditation and Framework Controls
Meeting regulatory standards—such as NIST 800-53 and the Risk Management Framework (RMF)—means selecting vendors versed in compliance and security landscapes. High-quality images are built to satisfy framework controls and come with documentation and templates that directly address audit and regulation needs. Relying on industry-standard formats (like Red Hat RPM) enables safe customization while supporting streamlined integration and better outcomes.
Ensuring STIG, FIPS, and SLSA Compliance for Critical Operations
Regulated entities, especially within the U.S. public sector, must comply with Security Technical Implementation Guides (STIGs) and associated guidelines. Vendors providing “STIG Ready” content simplify the path to compliance and risk management. On the cryptography front, Federal Information Processing Standards (FIPS)—specifically 140-2 and 140-3 set foundational requirements for secure information handling, trusted by both government and commercial organizations.
Supply-Chain Levels for Software Artifacts (SLSA) further reinforce security with traceable provenance from source to binary. Meeting SLSA Build Level 3 ensures distributed software can be validated for origin, integrity, and build process transparency.
Supporting Disconnected and Air-Gapped Environments
Federal agencies and high-compliance sectors frequently require operational isolation to protect sensitive data. Disconnected networks—physically separated from external connections offer strong defense against remote exploitation. Supply chain security strategies must address the challenges of updating air-gapped systems, providing procedures and tooling for timely CVE fixes. Solutions like Bitnami charts-syncer help seamlessly move packages across boundaries, ensuring compliance and security continuity.
Automating Documentation for Rapid Compliance and Recovery
Modern enterprises and agencies increasingly require automated generation of compliance documentation, including SBOMs, VEX statements, and provenance attestations. Automation reduces audit complexity, accelerates vulnerability response, and supports ongoing standards adherence. This holistic view is essential for both reacting to incidents and maintaining continuous compliance.
From Building Blocks to Comprehensive Security
Achieving supply chain security now requires an integrated approach—deploying the right mix of hardened containers, curated catalogs, compliance-ready images, and automated documentation. As cloud-native and platform-as-a-service patterns mature, organizations must architect systems for seamless, omnipresent security. The result: faster releases, improved developer satisfaction, and resilience in the face of new threats and evolving regulatory demands.
Read more such articles from our Newsletter here.