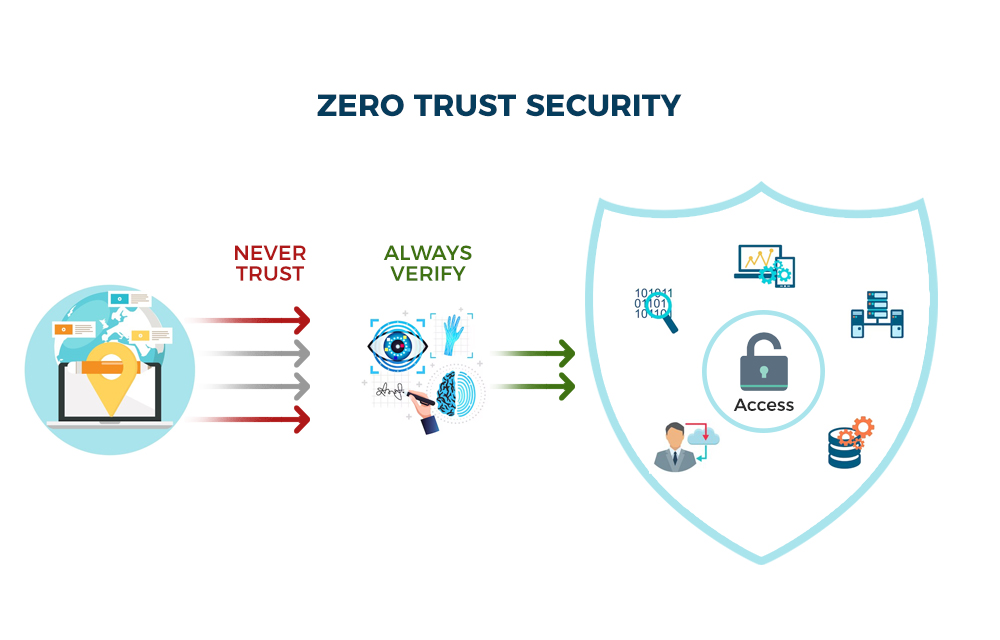
Modern work patterns place data on personal laptops, cloud containers, and partner portals. Unsurprisingly, malicious actors have too big of an attack surface for perimeter firewalls to watch them all. Zero trust architecture emerged as the default answer to these gaps. It treats every request as untrusted until it passes a policy check that considers identity, device health, and the resource in question. It rejects the idea that traffic is safe just because it comes from a corporate network. On the contrary, it checks each action in real time, records the result, and uses that data to improve future checks. As a result, the system adapts iteratively as users move and workloads change.
Regulators now embed zero trust into compliance frameworks. Hence, boards link funding decisions to clear verification milestones and transparent audit readiness. Let’s explore it in greater detail:
Core Principles of Zero Trust
Zero trust network architecture is based on three interlinked principles:
- Verify explicitly
- Limit privilege
- Watch continuously
Users need to authenticate with multifactor, devices report health, and the policy engine reviews context before allowing or denying. Next, the permissions must match the current task, so even a valid user cannot read payroll data while examining marketing metrics. Lastly, the monitoring engines measure traffic patterns, compare them with known baselines, and surface anomalies for rapid action. Because each principle supports the others, the system grows stronger over time: verification ensures correct identity signals, least privilege restricts lateral movement, and monitoring supplies evidence that fine-tunes future policies.
Because users shift contexts during a workday, the policy engine recalculates privilege at session renewal, which keeps scopes aligned with the person’s purpose.
Key Components of a Zero Trust Architecture
Identity systems keep the official record of who a user is and what device they’re on. Every time someone tries to connect, that information is checked by a policy engine to decide if the request is allowed. Gateways then apply that decision in real time.
The network is broken into smaller zones so attackers can’t move from a public website into sensitive systems like payments. Activity is constantly logged and analyzed for risk. If suspicious activity appears, the system can block access, quarantine the device, or require extra authentication. Auditors can then review the logs to confirm who accessed what and whether it complied with policy.
Configuration management databases feed asset tags into claims, allowing the policy engine to spot unregistered hosts and quarantine them before they request sensitive resources.
Implementing Zero Trust: Step-by-Step
Start with discovery. You inventory users, endpoints, workloads, and data flows because you cannot protect assets you cannot see. With that map in hand, modernize identity by enabling single sign-on, multi-factor prompts, and device registration. Next, create small trust zones around high-value assets, then direct traffic through context-aware gateways.
Write policy statements that test user role, device health, and resource sensitivity instead of source IP ranges. Introduce continuous monitoring by streaming authentication logs and network flow data into an analytics layer. Establish baselines over thirty days, then set thresholds for unusual activity such as impossible travel or sudden data exfiltration. When alerts are triggered, the automated runbooks revoke sessions, isolate machines, or roll back recent deployments as immediate measures. Expand these steps zone by zone until every decision relies on real-time context rather than on physical location.
A common pilot starts with developer laptops and a single internal Git service; early success then builds support to extend controls into APIs.
Benefits of Zero Trust Architecture
Precise verification lowers attacker dwell time because a stolen password fails device posture tests and privilege checks. Limited permission sets curb insider risk, as employees see only what their current role requires. Real-time analytics reduce detection intervals from days to minutes, which cuts recovery costs. Policy engines store a complete audit trail, helping you satisfy regulatory demands without manual log digging. Business units move faster because security controls travel with identities. When a developer spins up a container in a new region, policy gates cover the instance automatically, so projects launch without firewall change requests. Each of these improvements compounds the next: fewer incidents mean less rework, which frees time for product improvements that ultimately keeps the organization competitive.
Finance teams see lower unplanned outage costs, and partners integrate faster because standardized token formats eliminate weeks of custom firewall rule reviews.
Challenges and Limitations
As good as it sounds, zero trust architecture is not without its limitations. Unmanaged devices often evade the oversight, leaving blind spots in verification. Legacy systems that are locked to fixed IP addresses seldom fit micro-segmented networks. This forces teams to rely on interim proxies. And when authentication prompts fire too often, people get irritated and help-desk is compelled to do the firefighting.
Collecting and analyzing telemetry needs a handsome budget and skilled people; resources smaller teams rarely have. Momentum often fades when app owners worry that the new gateways will slow their services. As with everything, starting with small pilots, expanding in stages, and sharing clear results keeps the rollout on track in such scenarios.
Operational technology in factories often runs on archaic, fragile protocols, and inserting deep packet inspection may disrupt production lines. This would take the engineers to validate timing tolerances, thereby offsetting the negative impact.
Zero Trust vs Traditional Security Models
A bank might lean on zero-trust checks to keep its payment streams safe from credential stuffing and insider fraud. A hospital could apply the same ideas to electronic health records, meeting strict privacy rules and producing the audit trails inspectors expect.
A tech firm with employees spread across the globe can swap its clunky VPN tunnels for zero-trust gateways. This will give teams secure cloud access without the usual slowdown. Government agencies can follow suit to satisfy identity-centric rules that span on-prem systems and public clouds.
Even a factory can benefit: by inserting a lightweight gateway that turns old industrial protocols into authenticated traffic, manufacturers keep ransomware away from programmable controllers and the production line stays on schedule.
Conclusion
A zero trust architecture brings fine-grained control to every connection. By verifying explicitly, limiting privilege, and watching continuously, you prevent uncontrolled lateral movement and shorten incident response. Implementation calls for accurate inventories, modern identity foundations, and robust monitoring, yet the payoff justifies the effort. When policy adapts to context and every session must pass a fresh check, breaches lose momentum, operations stay agile, and security aligns with how modern organizations work rather than hindering progress.
The journey stays iterative; each finished segment strengthens the whole, so steady momentum beats ambitious scope when rolling zero trust security architecture.



